Just one circumstance I see usually with customers is the want to management and monitor file downloads from the cloud. For most corporations in most industries, it’s significant to regulate your organization’s information, and that information is typically contained in data files. The proprietary nature of information in data files tends to make them extremely valuable to several corporations, and thusly vital to command.
In this blog site write-up, I’m going to get started searching at the options that Microsoft Defender for Cloud Applications has offered to help your organization superior regulate and monitor file downloads.
Checking mass file downloads
Microsoft Defender for Cloud Apps (DCA) tends to make checking and making use of some management in excess of mass downloads very simple to get started.
The DCA portal can be accessed at portal.cloudappsecurity.com.
To speedily get started out with checking mass downloads by a one user, Microsoft has presented a straightforward to use template:
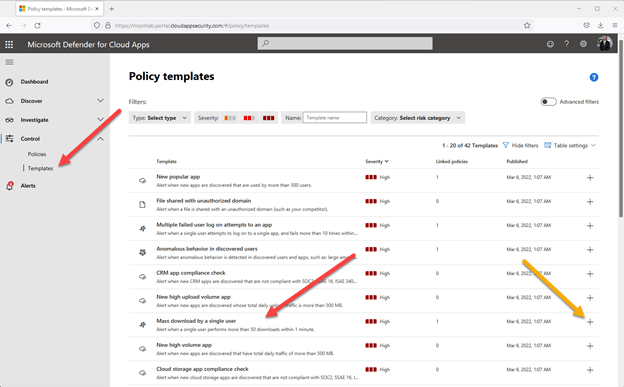
Figure 1 – DCA portal for templates
In the figure higher than, you can see I have navigated to Regulate > Templates and found the default template named “Mass down load by a single consumer.” The inexperienced arrow details to the “+” button to use this template.
Working with the “+” button will start a wizard to produce a new exercise plan based mostly on the template:
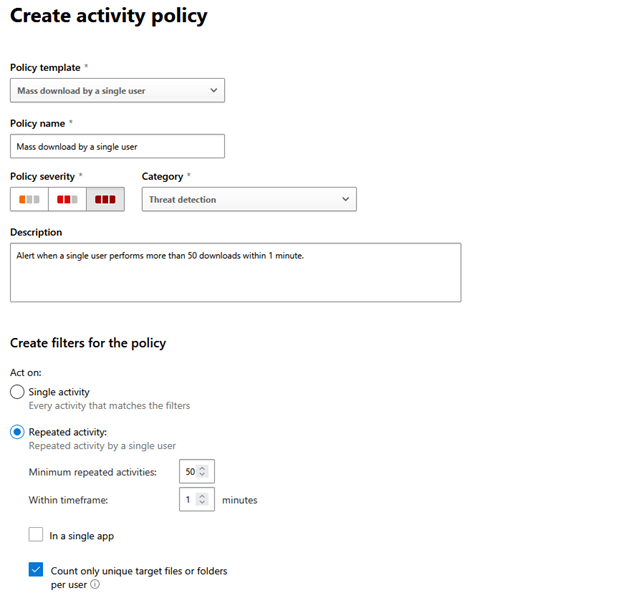
Figure 2 – New action policy from template
At the prime it reveals the template utilized to generate this policy, and beneath that you’ll see “Policy name”. You can name the policy no matter what operates for your group, and the description should really be used to ensure every person is aware of your intention with this policy. In addition to such as a very good description of the supposed function for this policy, I suggest including information and facts about who established this policy and when it was made.
The plan severity and group containers really do not have a specialized effect at this position but can be significant to the operate of DCA with other instruments. A lot more on that later, but for now choose solutions that make feeling for your group.
The “Create filters for the policy” section is where by we get started our configuration. For this policy we want to retain the “Repeated activity” radio button, but your corporation might want to adjust the thresholds. I have the “Minimum recurring routines:” and “Within timeframe:” established to 10 in 1 minutes in my tenant, but that is generally for screening purposes. The two check boxes under that are self-explanatory.
The future portion of the template is the activity filter:
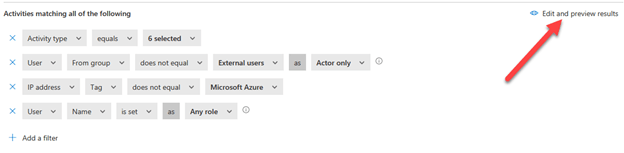
Figure 3 – Policy filters
The filters in this template are pre-built for you as demonstrated above, and most typically a fantastic starting up level:
- Activity variety is the exercise monitored by this plan. The “6 selected” pull down will show you this template functions versus file downloads.
- Consumer is the filter for whom this coverage applies. The template applies to all people in your firm (excluding external buyers) as the true account undertaking the file obtain.
- IP address filter excludes downloads that originate from Azure alone.
- Consumer involves all consumers in this case.
The arrow in figure 3 details to the “Edit and preview results” wizard. Clicking there will open up a new window that demonstrates you which logged actions would be provided in this filter as shown down below:
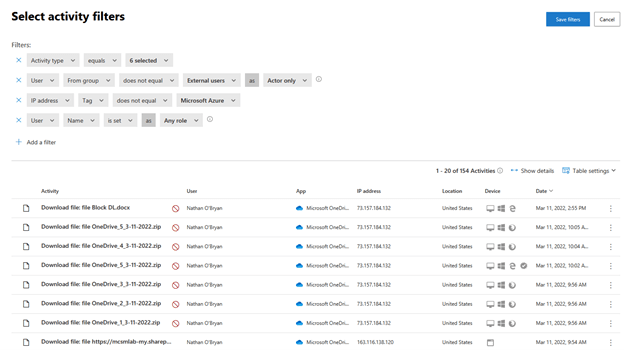
Figure 4 – Filter results
The filter reveals which activities this plan would have an effect on. The red circle with the line by way of reveals if that exercise was successful.
The upcoming area is for alerts:
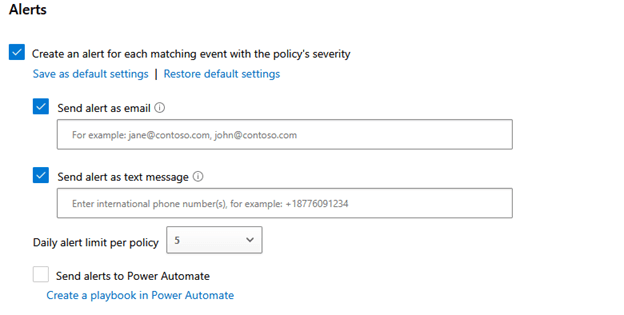
Determine 5 – Alerts
The alerting has 3 options: e mail, textual content message, and Electricity Automate. In my testing I have uncovered that none of these selections are nearly anything near to “real time.” These alerts can choose from minutes to hrs to present up, so never count on DCA for authentic-time alerting. I have not but experimented with to do everything with the alerts to Electricity Automate, but I suspect there are great uses for that attribute.
The final area of the plan is for Governance actions:

Figure 6 – Governance steps
This area of the policy can enable you to just take true steps past just checking action. You can use this coverage to reduce consumers from mass downloading information based on what you configure here. The “All apps” area applies to all apps that DCA is aware of about, and the Office 365 area applies to only Office environment 365 apps:
- Notify user tells the person they have accomplished an motion that matches this coverage. In my belief this is a should for most implementations. Don’t forget that there are means about these protections, and our major goal with this coverage really should be to maintain straightforward people sincere. Checking this box allows you to enter a personalized notification message for this alert.
- Notify additional customers notifies someone else. Probably a compliance manager and/or administrator. You can choose many accounts to notify right here.
- Suspend person blocks the person who triggered this coverage from using the software they ended up employing though triggering this policy.
- Have to have person to indicator in all over again invalidates all of that user’s tokens issued by Azure Advertisement. This will drive them to indication in all over again to M 365 and any other applications they have signed into by way of Azure Advert. The big advantage here is that user will have to authenticate in opposition to your Conditional Access guidelines yet again, which may perhaps implement in a different way in predicaments the place the user has logged in with 1 established of problems but is accessing information with a unique established of ailments. Most handy for a person who logs into a notebook or mobile product in just your company community, but then tries to obtain documents from one more unprotected network. Continuous Entry Analysis may well also present the identical functionality.
- Verify consumer compromised sets the user’s danger level to substantial, which can induce other actions from other protection functions or DCA policies.
The three verify packing containers beneath “Office 365” consider the same actions as the exact buttons in the “All apps” portion, but they only use to Office environment 365 programs.
What is the effect?
As I have configured this coverage, all it does is give a notification of mass file downloads by a single person. In my tests, these notifications can get various several hours to show up.
My advice for an administrator whose organization is intrigued in utilizing download controls within just an M 365 tenant would be to start off right here. Set up a plan like this to see how mass downloads are transpiring in your tenant, then determine about how to limit these downloads.
After you have set up a notify coverage like this and allow it run for a though, you are going to have a good idea of how typically users are downloading significant quantities of information and your administration can make some choices about how substantially of a hazard this is, and how your group desires to restrict people mass downloads.
In foreseeable future blog posts, I’ll dive into preventing end users from downloading big figures of data files at once.
Trade Hybrid and Office 365 Monitoring and Reporting
On-premises parts, such as Ad FS, PTA, and Exchange Hybrid are important for Business office 365 conclusion user encounter. In addition, some thing as trivial as expiring Exchange or Ad FS certificates can certainly direct to surprising outages. By proactively monitoring hybrid components, ENow gives you early warnings in which hybrid elements are reaching a critical point out, or even for an approaching expiring certification. Realizing immediately when a dilemma takes place, where the fault lies, and why the situation has occurred, ensures that any outages are detected and solved as quickly as attainable.
Access your no cost 14-working day trial of ENow’s Exchange Hybrid and Business 365 Monitoring and Reporting right now!

More Stories
Elevate Your Lifestyle: Why Google Smart Home Technology Makes Every Moment Easier
Transform Your Living: Discover the Incredible Power of Smart Home Management for Effortless Comfort
Unlock Pure Comfort: The Powerful Ways an Alexa House Simplifies Modern Living